Bugdar Documentation
1. Create an Account
First, create your Bugdar account:
2. Install GitHub App
To analyze pull requests, you need to install the Bugdar GitHub App in your repositories:
- Goto your Bugdar Profile Page
- Find the "Install GitHub App" button
- In GitHub, select the repositories you want to analyze, or select all
- Successful confirmation should return you back to Bugdar Profile Page
3. Obtain API Token
Use the API token for integration with the Bugdar API for CI/CD pipelines or other integrations.
Genearte an API token via the Usaer Profile Page or:
Generate an API token to authenticate your request with the API:
POST /api/tokens Authorization: Basic base64(username:password)
Store the returned token securely. All subsequent API requests should include this token in the Authorization header:
Authorization: Bearer YOUR_API_TOKEN
4. Optionally setup Slack Notifications
To receive notifications in Slack, you need to setup the Slack App in your workspace:
- Goto your Bugdar Profile Page
- Find the "Setup Slack Notifications" button
- Follow the instructions to complete the setup
Pull Request Analysis Flow
When a pull request is created or updated, Bugdar automatically processes it through the following steps:
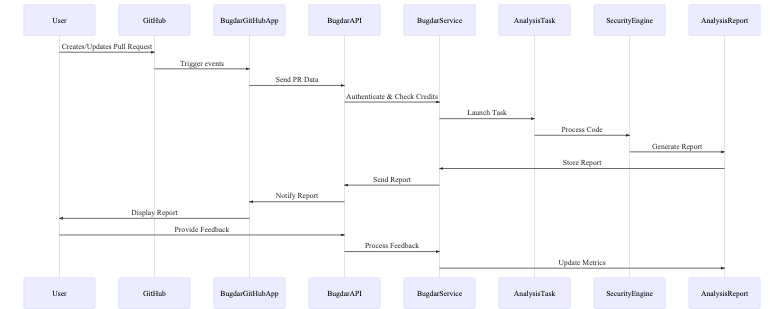
Key Entities:
- GitHub: Source code hosting platform where pull requests are created and managed
- Bugdar GitHub App: Our GitHub integration that receives webhook events and interacts with repositories
- API Gateway: Entry point for all webhook events, handles authentication and request validation
- Task Queue: Manages asynchronous processing of analysis requests
- Analysis Engine: Core component that performs security analysis on code changes
- Notification Service: Handles delivery of analysis results through various channels (GitHub, Slack)
Process Overview:
- Developer creates or updates a Pull Request in GitHub
- GitHub sends webhook event to Bugdar GitHub App
- API Gateway authenticates the request and validates organization credits
- Task Queue receives analysis request and schedules processing
- Analysis Engine retrieves PR changes and performs security analysis
- Analysis results are stored and sent to Notification Service
- Notification Service posts comments to GitHub PR and sends configured alerts
- Developer reviews analysis results and provides feedback
Source Code Analysis Flow
For direct source code analysis through the API:
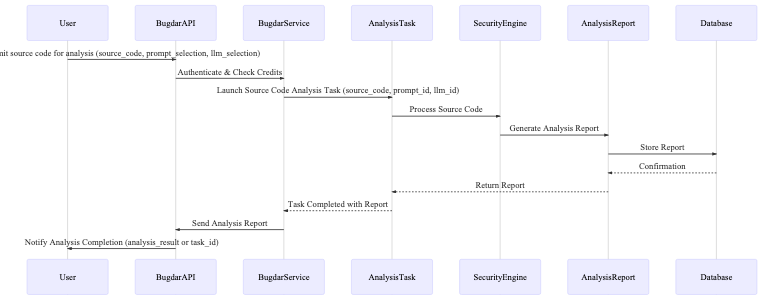
Key Entities:
- Client: External system or tool making API requests
- API Gateway: Handles authentication and request routing
- Analysis Engine: Processes source code and generates security analysis
- Results Store: Persistent storage for analysis results
Process Overview:
- Client submits source code analysis request via API
- API Gateway validates authentication token and credit availability
- Analysis Engine processes the submitted code
- Results are stored and returned to client
- Client can retrieve historical results via API
Synchronous Analysis
POST /api/analyze/github-pr
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
{
"url": "GITHUB_PR_URL",
"prompt_id": "PROMPT_ID",
"llm_id": "LLM_ID"
}
Asynchronous Analysis (Background Task)
POST /api/analyze/github-pr-task
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
{
"url": "GITHUB_PR_URL",
"prompt_id": "PROMPT_ID",
"llm_id": "LLM_ID"
}
Analyze Recent Merged PRs
POST /api/analyze/github-merged-prs-last-n-days
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
{
"org": "github_org",
"repo": "github_repo",
"days": N,
"prompt_id": "PROMPT_ID",
"llm_id": "LLM_ID"
}
Create Prompt
POST /api/prompts
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
{
"action": "add",
"title": "Prompt Title",
"content": {
"role": "Security Analyst Role",
"task": "Analysis Task Description",
"vulnerability_scope": {
"IN_SCOPE": ["vuln1", "vuln2"],
"OUT_OF_SCOPE": ["excluded1", "excluded2"]
}
}
}
Update Prompt
POST /api/prompts
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
{
"action": "edit",
"prompt_id": "PROMPT_ID",
"content": "Updated content"
}
Delete Prompt
POST /api/prompts
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
{
"action": "delete",
"prompt_id": "PROMPT_ID"
}
Get Repository Config
GET /api/repository/{repository_id}
Authorization: Bearer YOUR_API_TOKEN
Update Repository Config
POST /api/repository/{repository_id}
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
{
"prompt_id": PROMPT_ID,
"llm_id": LLM_ID,
"github_comments_enabled": true
}
Generate New Token
POST /api/tokens Authorization: Basic base64(username:password)
Revoke Token
DELETE /api/tokens Authorization: Bearer YOUR_API_TOKEN
Analysis costs are calculated based on token usage at a rate of $0.12 per 1,000 tokens. The total tokens used depends on the size and complexity of the pull request being analyzed.
Example calculation for 500 tokens: (500 / 1000) * $0.12